Windows XP Sniffer Documentation
August 27, 2003
August 27, 2003
GV/WFL BOCES EduTech
GV/WFL BOCES EduTech
Windows XP Sniffer Instructions
Windows XP Sniffer Instructions
Activation
Activation
To turn on firewall logging, perform the following steps.
1. Right click on My Network Places and select Properties
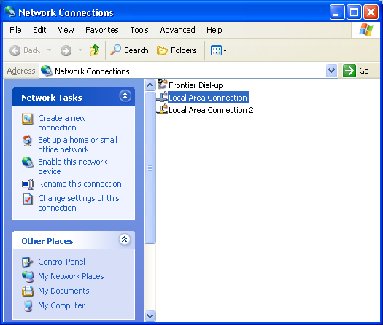
2. Select Local Area Connection.
3. Right click and select Properties.
4. Select the Advanced Tab
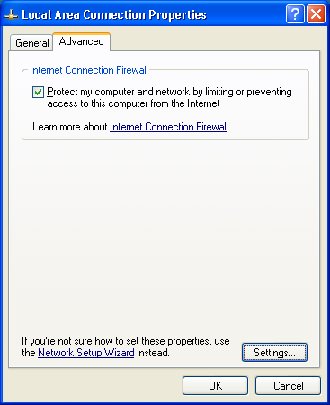
5. Check the Protect my computer and network by limiting or preventing access to this computer from the Internet
6. Click the Settings button.
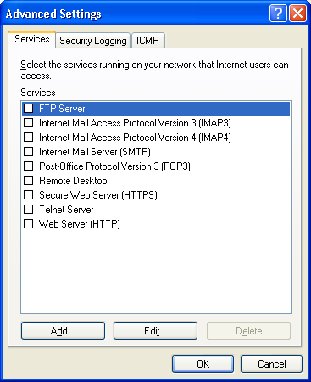
7. Select the Security Logging Tab.
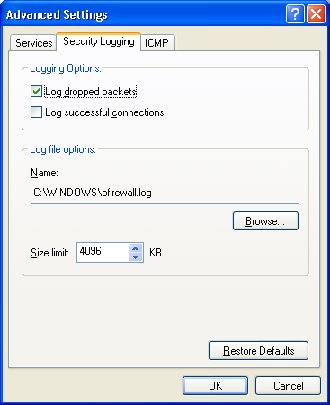
8. Under Logging Options, check the Log dropped packets option.
9. Make a note of the log file name (pfirewall.log) and path for future use.
10. Click Okay as needed to close the open windows.
A log file will be created as a Microsoft Notepad file. To view the log file, follow the path that was specified in step 7 above. Using the path specified as an example, you might do the following.
�
Open My Computer
�
Select the C drive
�
Open the WINDOWS folder
�
Find the pfirewall.log file and open it.
The log file will continue to grow indefinitely unless the monitoring is halted. After a sufficient amount of data has been logged, turn off the logging utility by reversing the settings established in Steps 1 through 8 above.
Reading the Log File
Reading the Log File
The log file will look like this in Microsoft Notepad.
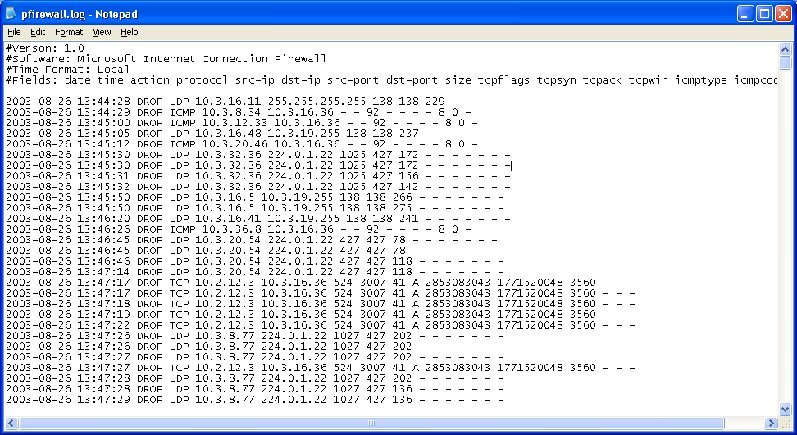
Search for ICMP Protocol codes and a Size of 92. These are the field parameters that will indicate the possibility of the welchia virus running on a computer with the indicated src-ip.
Bringing the Data into Excel and Sorting
Bringing the Data into Excel and Sorting
If the log file is large, you may wish to move the data into Microsoft Excel to use advanced sorting or filtering capabilities.
1. Open a blank spreadsheet.
2. Go to File and then select Open
3. At the bottom of the Open window, change the Files of Type dropdown window to read All Files (*.*)
4. Either enter the path and file name of the log file or use the browse features to find and select the file.
5. When Excel opens the file, it will recognize that it is not an Excel formatted file and give you the option of delineating the text with the Text Import Wizard.
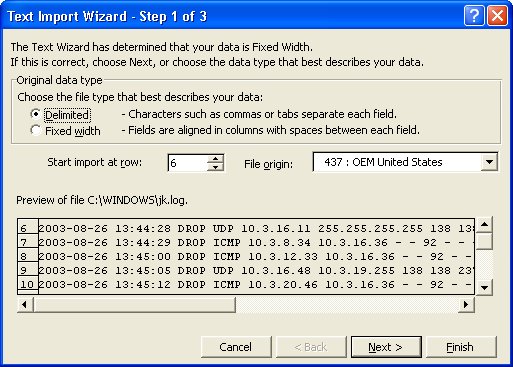

6. Choose the Delimited file type and Start the import at row 6 to avoid the header information.
Note: If you want to retain the column headings, start the import at row 4 but remember that all names will be shifted to the right by one column because of the “#Fields:” in that line of text.
7. Click on Next
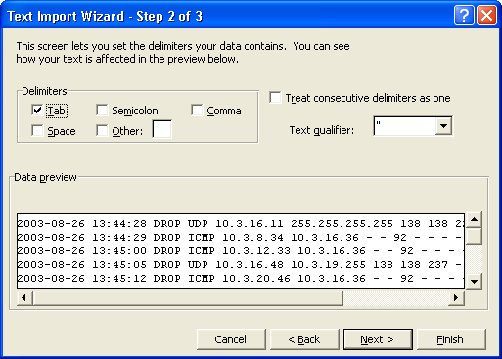
8. Now Change the Delimiters selection from Tab to Space
From This
To This

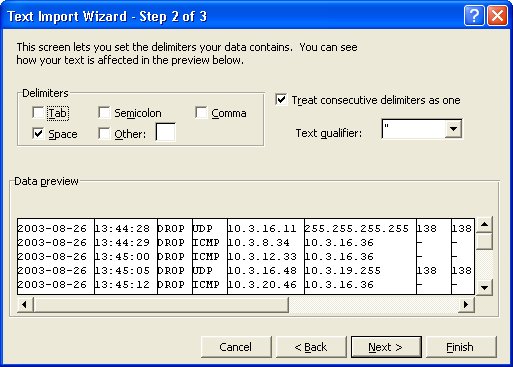
9. Now click on Next again.
10. No need to change data formats as provided by step 3 of the Wizard. Just click Finish.
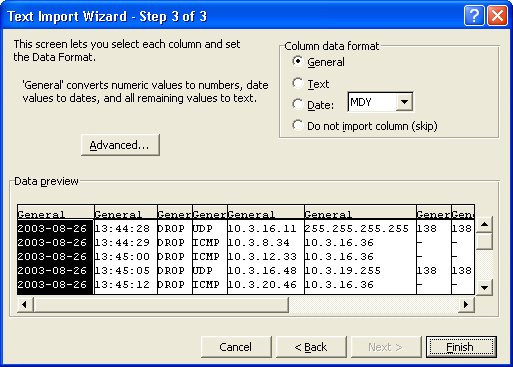
The spreadsheet will open as shown.
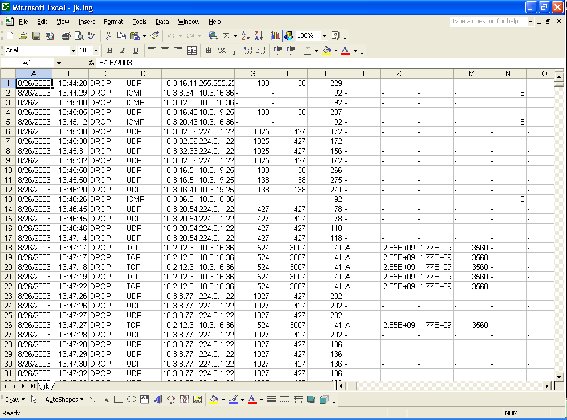
To sort the data in Excel:
1. Select the entire spreadsheet by clicking in the upper left corner of the sheet.
2. Click on Data on the top menu and pull down to select Sort.
3. You will see the following window:
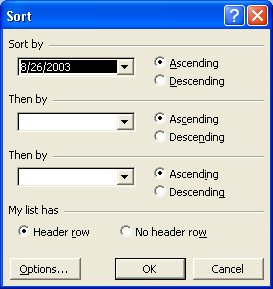
4. First select My list has (No header row).
5. Now, the Sort by box will contain the column names. Select column D. This is where the Protocol data is located.
It will now look like this:
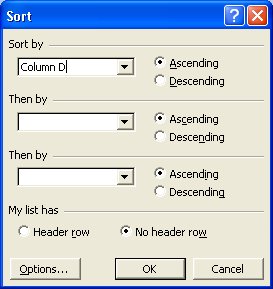
6. Click on OK.
7. The columns will now be sorted by Protocol and the ICMP designations will all be together for easy location and further analysis.
Tracing IP numbers
Tracing IP numbers
Once a suspected machine has been identified by the src-ip number provided by the log file, a trace route may be performed to obtain location information.
1. Click on the Start button and select Run.
2. In the space provided, enter Command as shown and click OK.
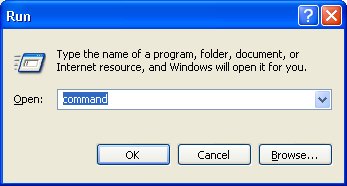
3. The following Command Entry Window will be displayed.
4. At the
C:\>
enter the trace route command (tracert) followed by the IP address you wish to trace. For example, to trace IP address 10.3.36.8, the command would look like this:
C:\>tracert 10.3.36.8
5. Press enter and the trace will begin. Results will be displayed as shown on the next page.
Results of a tracert command on IP number 10.3.36.8

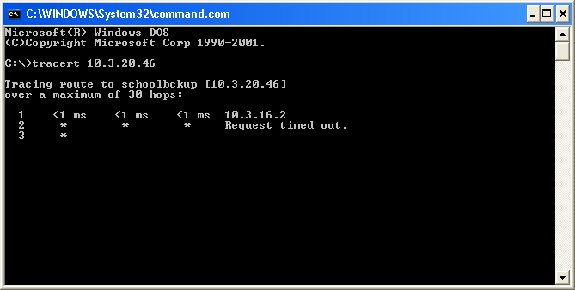
The trace was able to provide the machine name, in this case, schoolbckup
The trace will continue to run for 30 hops.
To halt the process, press CTRL-Break.
 In the screen shot below, the original trace was halted and another was initiated for IP 10.3.8.34 resulting in the computer named wflboces-118980 being identified.
In the screen shot below, the original trace was halted and another was initiated for IP 10.3.8.34 resulting in the computer named wflboces-118980 being identified.

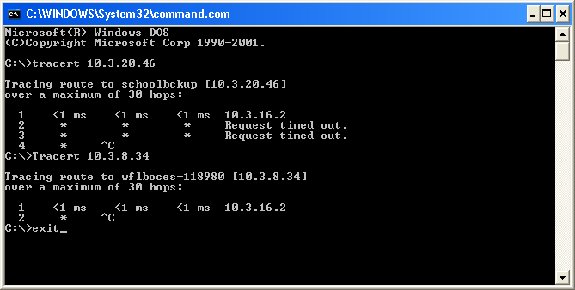
Finally, as displayed above, you must issue an Exit command to close the window.




















